TL;DR it was more tedious than expected
As a proud owner of an ACR122U NFC reader, I periodically try to read the content of my own cards, out of interest. This device can only work on the 13.56 MHz and is fairly limited compared to a Proxmark3, but is much cheaper, which is also an important factor to the broke penetration tester that I am. You can find one on Amazon for less than $30; however, be careful to avoid chinese conterfeit devices, as the hardware is not always correctly supported by the libnfc drivers.
Please let me in
It had been a while since the last time I used it, but I was pretty confident about my memories regarding Mifare cracking. So i fired up mfoc, to try and dump the content of the targetted card using the usual default keys. Unfortunately, the card did not use any of them.
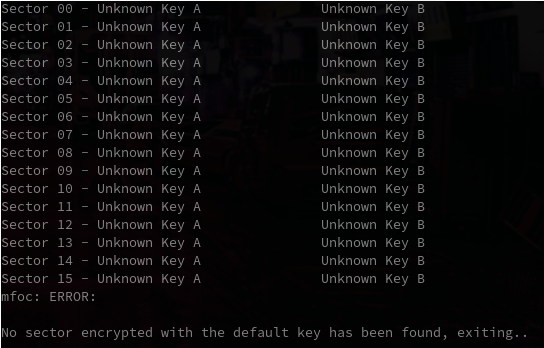
Well that's a shame, but we can deal with it. I moved on to the DarkSide attack using mfcuk.
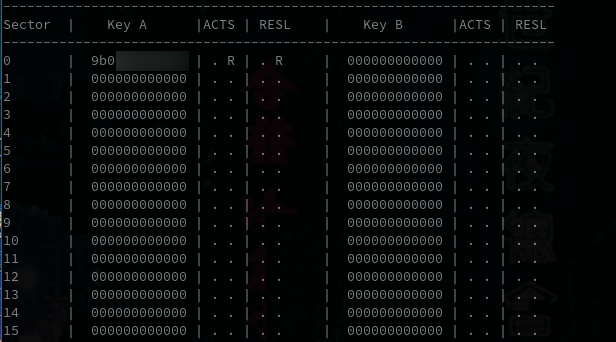
So far, so good !
Oh boy.
Well that was unexpected. Somehow, the key that had been recovered by mfcuk is faulty and cannot be used in a nested attack with mfoc (I later realized that only the last bytes of the recovered key were correct). I use archlinux with the blackarch repositories, so the installed version is 0.3.8-8, which seems broken with ACR122U, most likely because of this issue. Unfortunately, many people seemed to have the same issue, even using newer versions of mfcuk. Loooking up the internets using the almighty search engine, I stumbled upon this Gist which gives us a good match between mfcuk r65 and libnfc 1.5.1. Of couse, you can find a curated script here, to save you the hassle of compiling.
Finally!
Alright, let's mf**k this tag. Please follow the exact instructions below, in this precise order and as root, or something, somehow, somewhere will go wrong.
- Blacklist the drivers that may interfere with the reader
echo "blacklist nfc" > /etc/modprobe.d/blacklist-libnfc.conf echo "blacklist pn533" > /etc/modprobe.d/blacklist-libnfc.conf echo "blacklist pn533_usb" > /etc/modprobe.d/blacklist-libnfc.conf - Launch pcscd -f to make sure that the right drivers are properly loaded
- Plug in your NFC reader WITHOUT ANY TAG NEARBY and wait for it to initialize (fix red light)
- Put the tag you want to copy on the reader (the light should turn green)
- Use DarkSide attack to recover one key with mcuk
LD_LIBRARY_PATH=whereveryouputyourlibs/builds/nfc/libnfc-1.5.1/libnfc/.libs mfcuk-r65/src/mfcuk -C -R 0:A -s 250 -S 250 -v 3
- Once your first key is recovered, use mfoc to perform a nested attack (your reader might be freezed at this point so you may want to perform steps 2 to 4 one more time)
mfoc -k yourrecoveredkey -O mifare.dmp
- Flash your card with the dumped data (including the UID)
nfc-mfclassic W ab chinese_card.dmp mifare.dmp
- Open only your own door, I am not liable in case you are trying to do anything illegal
Bonus track
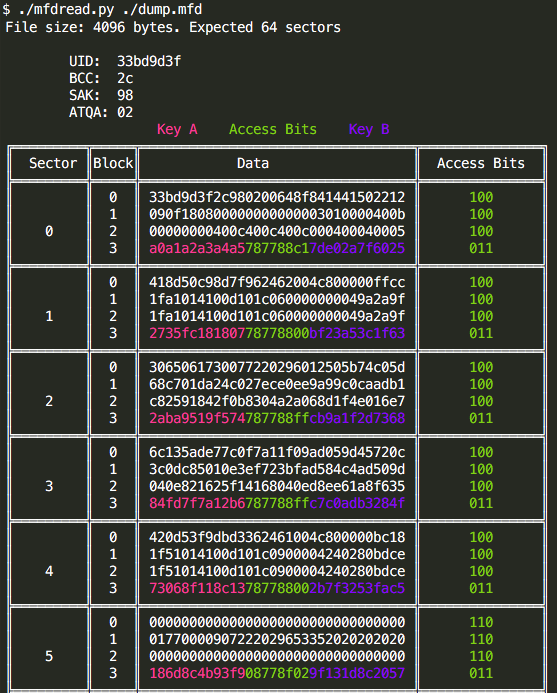
If your eyes do not parse your card's hex data natively, you can display it in a nearly human friendly format using the excellent mfdread which makes the memory layout crystal clear.
Need offensive security services, or application security support? CryptID has got you covered!
